Attack surface management | In the cybersecurity landscape, organizations face a relentless onslaught of threats from sophisticated hackers.
These adversaries are constantly probing for vulnerabilities, seeking to exploit any weakness to gain access to sensitive data and disrupt operations.
To stay ahead of this relentless pursuit, organizations must adopt a proactive approach to cybersecurity, starting with a comprehensive understanding of their attack surface.
What is Attack Surface Management?
Attack surface management (ASM) is the systematic process of identifying, monitoring, and controlling all assets and potential entry points that could be exploited by attackers.
It’s about gaining a holistic view of your digital footprint, encompassing everything from traditional IT infrastructure to cloud-based applications and even physical devices.
Why is Attack Surface Management Critical?
In today’s interconnected world, organization’s attack surfaces are expanding at an unprecedented rate.
The proliferation of devices, applications, and cloud services has created a vast network of potential targets for hackers.
Without effective Attack Surface Management (ASM), organizations are essentially playing a game of whack-a-mole, constantly reacting to breaches rather than proactively preventing them.
The Benefits of ASM
Implementing a robust ASM program offers numerous benefits, including:
- Reduced risk of breaches: By proactively identifying and addressing vulnerabilities, organizations can significantly minimize the likelihood of successful attacks.
- Improved incident response: With a clear understanding of their attack surface, organizations can respond to breaches more quickly and effectively, minimizing damage and downtime.
- Enhanced compliance: ASM can help organizations meet compliance requirements by ensuring that their security posture aligns with industry standards and regulations.
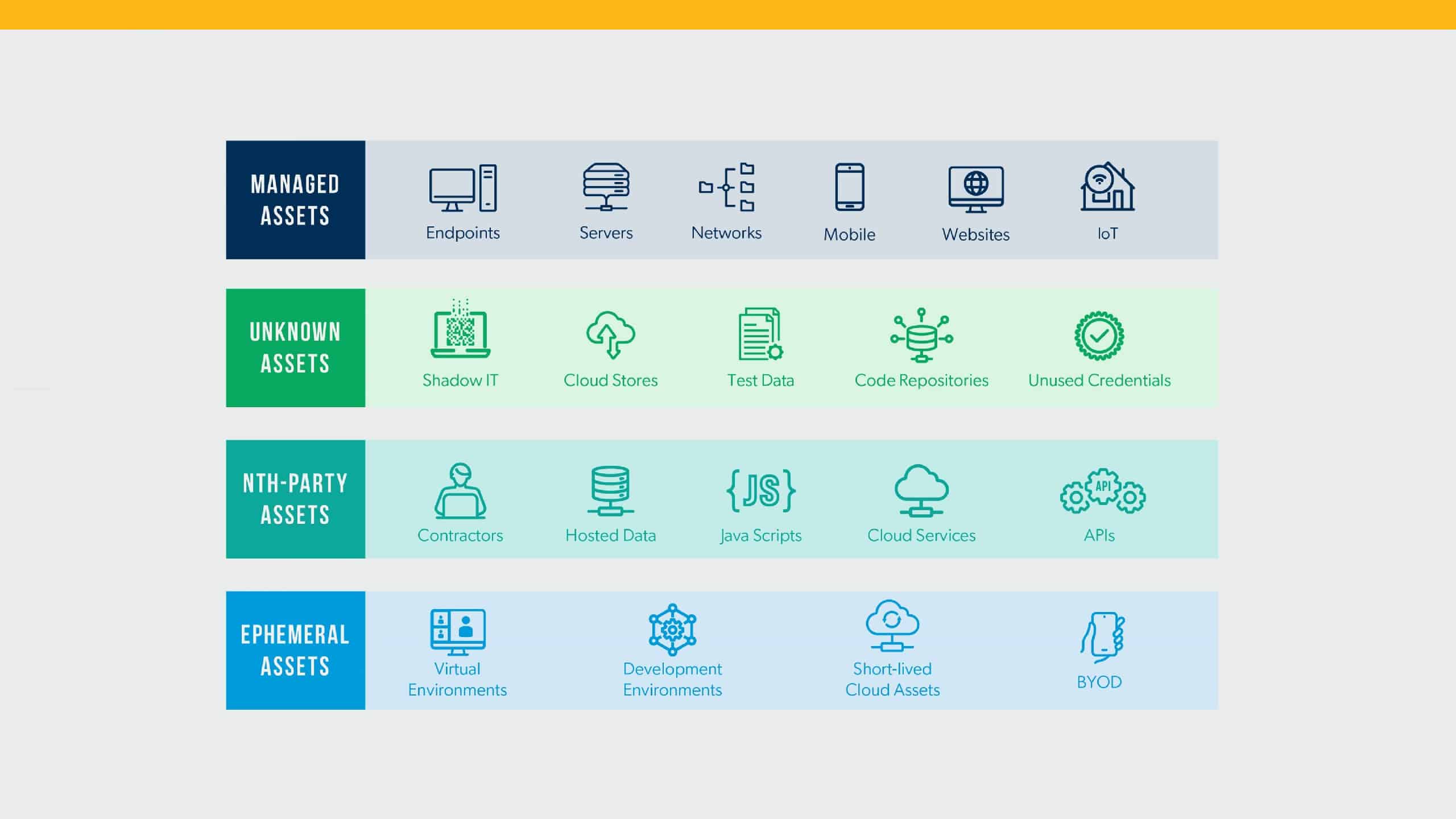
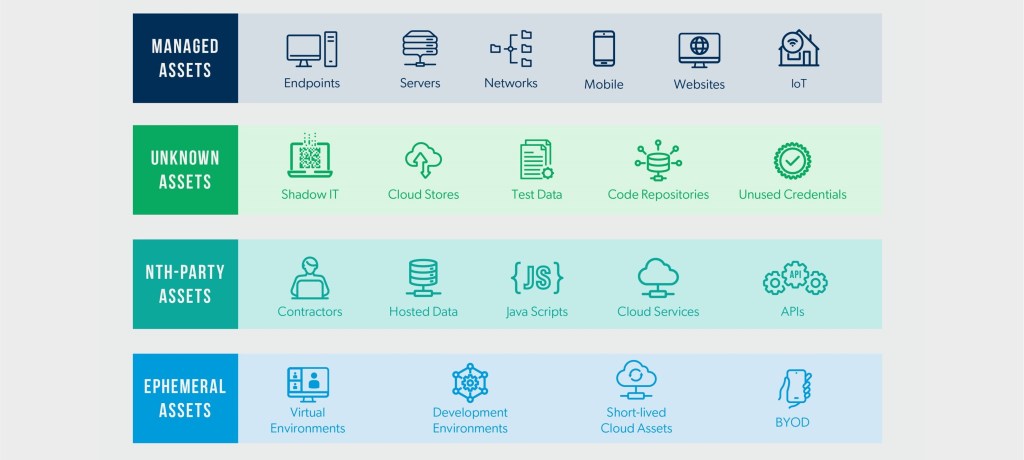
Finding Your Assets
The first step in implementing ASM is to conduct a thorough asset discovery process. This involves identifying and inventorying all assets within the organization, including:
- IT infrastructure: Servers, workstations, network devices, and other hardware components
- Software applications: On-premises and cloud-based applications, including web applications, APIs, and mobile apps
- Data: Sensitive data stores, such as databases and file servers
- Physical devices: IoT devices, smartphones, and other endpoints
Prioritizing Assets
Once assets have been identified, they need to be prioritized based on their criticality and risk level. This involves considering factors such as the sensitivity of the data stored on the asset, its connectivity to other systems, and its potential impact on business operations.
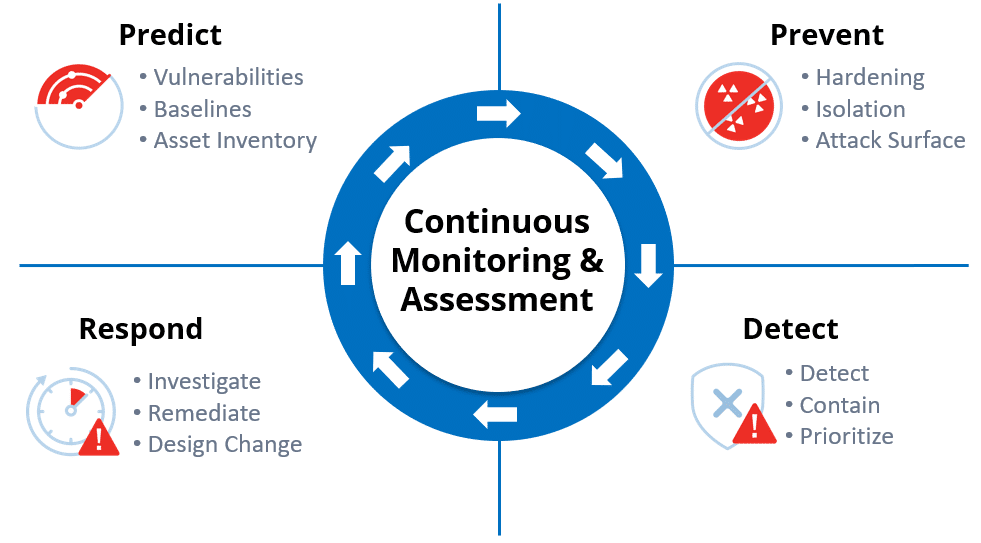
Monitoring and Remediation
ASM is an ongoing process that requires continuous monitoring and remediation. Organizations should regularly scan their assets for vulnerabilities and implement timely patches and updates to address identified risks. Additionally, they should implement access controls and other security measures to protect sensitive assets from unauthorized access.
ASM Tools and Solutions
Several ASM tools and solutions are available to help organizations automate and streamline the ASM process. These tools typically offer capabilities such as:
- Asset discovery and inventory: Automatically identifying and inventorying assets across the organization.
- Vulnerability scanning: Scanning assets for known vulnerabilities and providing remediation recommendations.
- Risk assessment: Prioritizing assets based on their criticality and risk level.
- Continuous monitoring: Continuously monitoring assets for new vulnerabilities and changes in their security posture.
Conclusions
In today’s threat-filled cybersecurity landscape, organizations cannot afford to ignore their attack surface.
By implementing a comprehensive ASM program, organizations can gain control of their digital footprint, proactively identify and address vulnerabilities, and significantly reduce their risk of falling victim to cyberattacks. Embrace ASM and stay one step ahead of the hackers.