SUMMARY
Adware is software that displays annoying advertisements on your device. It displays ads and collects data about users in order to customize advertising on their devices. It can be bothersome and slow down your device. Some free mobile apps, for example, may include adware that displays pop-up ads on your phone’s screen. Adware prevention is far easier than removing it after the fact.
Introduction
Adware programs are sneaky little things that can infect your computer when you download freeware or shareware. They basically launch annoying ads and redirect your search results to some promotional websites. It’s like a hidden price you pay for using the free program.
Sometimes, a sneaky Trojan horse can secretly download an adware program from a website and install it onto your computer without you knowing it. Or, hackers can use browser hijackers to download the adware program by exploiting vulnerabilities in your web browser.
Who is Targeted
Adware can be a nuisance for both individuals and businesses, but the primary targets are usually individual users. Adware developers frequently use enticing offers such as free games, movies, or exclusive deals to entice users to download their malware.
How you get infected
There are two ways in which it can get onto a user’s computer.
Firstly, some freeware and shareware programs include Adware as a way to generate revenue, but they usually stop displaying ads once the software is purchased or registered. However, sometimes Adware utilities may remain installed even after the software is registered, and removing them may cause the program to malfunction.
Secondly, it can be installed without authorization when a user visits an infected website. This is often done through browser vulnerabilities and Trojan programs that install Adware stealthily, also known as Browser Hijackers.
How Adware works
Adware can show ads by downloading text and images from advertiser-owned servers or redirecting search requests to advertising websites.
What Adware does
Additionally, Adware collects information about the computer and user’s browsing habits, such as IP addresses, operating system and browser version, frequently visited sites, and search queries.
It’s important to note that Adware ONLY collects data with the user’s consent, unlike Trojan spyware programs.
Types of Adware
- PUPs: Potentially unwanted programs are any software that was installed on your device without your permission.
- Browser hijackers: Alter your browser settings without your knowledge or consent, typically affecting both your homepage and default search settings.
- Legitimate adware: Any online advertisement that does not contain malware
Real-world examples:
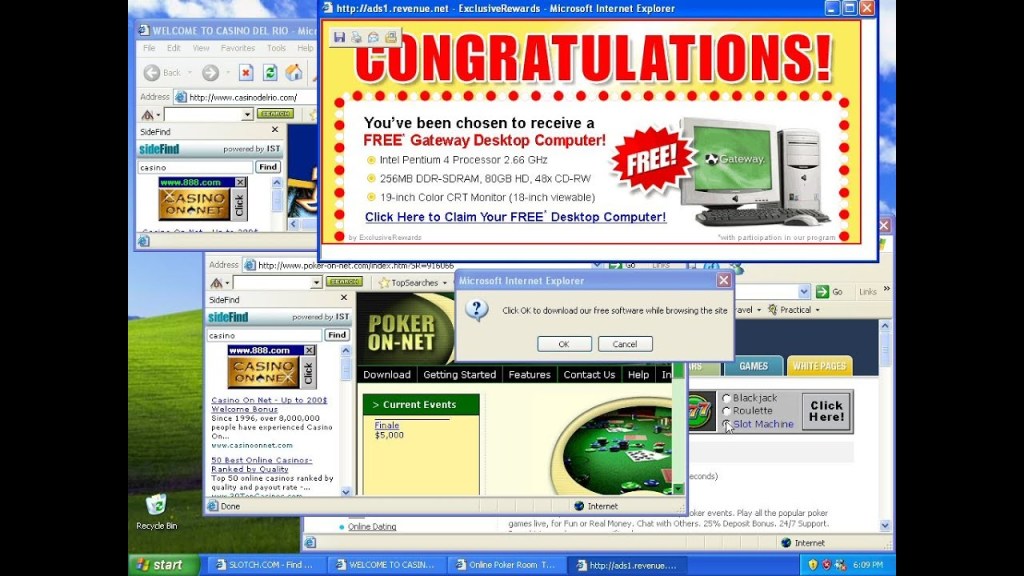
FakeAdsBlock – This malware pretends to be an ad-blocker app but actually displays high volumes of ads to Android device users.
HiddenAds – A family of adware-deploying trojans that hides within other apps, most commonly gaming apps. It was discovered in almost two-dozen apps in the Google Play Store, and more than seven million users downloaded the apps prior to their removal from the Play Store.
DeskAd – Starts as a relatively harmless ad-supported software, but later it redirects users’ web requests to malicious websites, adds buttons, toolbars, and links to browsers.
Shlayer – Targets MacOS devices and systems to install adware variants. In 2020, it was recognized as the “No. 1 Threat for Mac.”
How To Protect Yourself Against Adware
There are a few simple things you can do regularly to prevent your device from the invasion of adware:
- Make use of antivirus and anti-malware software
- Think before you click
- Only download from reputable sources
- Avoid freeware and shareware
- Make use of a reputable ad blocker
- Buy devices from reputable vendors
Take Away
If Adware collects information without notifying the user, it is considered a malicious program and falls under Trojan-Spy behavior. Adware benefits software developers by generating revenue and cutting costs, but it can also be a nuisance and compromise the user’s privacy.
Future-proof your business today.
CD CLOUD LOGIX — Trusted by 𝗕𝗲𝘁𝗳𝗮𝗶𝗿, 𝗠𝗼𝘁𝗼𝗿𝘄𝗮𝘆, and 𝗘𝘅𝗽𝗲𝗱𝗶𝗮.