As more and more businesses move to the cloud, it’s important to make sure that your internal REST API is properly secured.
What is A REST API?
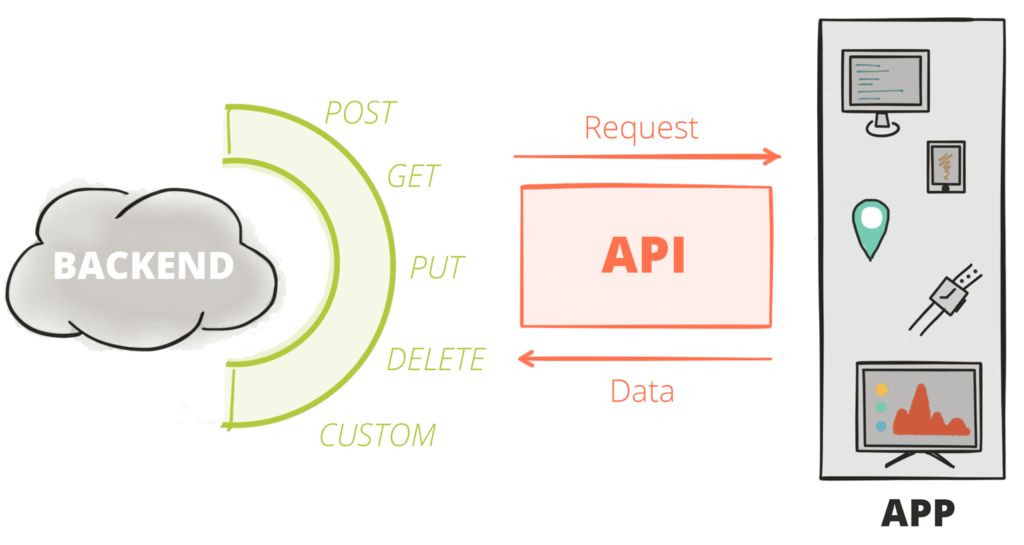
A REST API is an interface that allows two pieces of software to communicate with each other over the internet. The acronym stands for Representational State Transfer, and it defines a set of rules that govern how data is exchanged between software components.

A REST API can be used to access web services, databases, or any other type of resource that is accessible over the internet. In order to use a REST API, a client first needs to make a request to the server. The server then processes the request and sends a response back to the client. The client can then use the response to perform some action, such as displaying data on a screen or storing it in a database.
A REST API is a powerful tool that can be used to build sophisticated applications. When used correctly, it can make it possible for two pieces of software to interact with each other in ways that were not previously possible.
Here are some best practices to follow to secure you internal REST API:
Use TLS/SSL encryption for all communication.
Any time you’re sending sensitive information over the internet, you need to be sure that it’s properly encrypted. That’s why, if you’re using a REST API in the cloud, you should always use TLS/SSL encryption for all communication.
TLS/SSL is the gold standard for data encryption, and it will help to ensure that your data remains safe and secure. Even if someone were to intercept your data, they would not be able to read it without the proper decryption key. So if you’re looking to keep your data safe, be sure to use TLS/SSL encryption for all communication. It’s the best way to protect your data in transit.
Enable authentication and authorization for all users.
If you’re building a cloud-based application, you’ll likely need to expose some sort of REST API so that other applications can interact with your data. When doing so, it’s important to take security into consideration and make sure that your API is only accessible to authorized users.
The simplest way to do this is to enable authentication and authorization for all users. By requiring users to log in with a valid username and password, you can be sure that only those who are supposed to have access to your API will be able to use it. You can also use role-based authorization to further restrict access to specific parts of your API. By taking these measures, you can help keep your data safe and secure.
Keep your API updated with the latest security patches.
Your API is the lifeline of your business – it’s how you connect with your customers and partners. That’s why it’s so important to keep it up-to-date with the latest security patches. The last thing you want is for your API to be compromised by a hacker.
Luckily, there are a few easy ways to keep your API safe and secure.
- First, make sure you’re using the latest version of the software. This will ensure that you have the most up-to-date security features.
- Second, use a reliable cloud provider that offers security features such as encryption and two-factor authentication.
- Finally, consider using a dedicated API management platform to help you secure and manage your API. By taking these simple steps, you can rest assured that your API is safe and secure.
Use a web application firewall (WAF) to protect your API.
A web application firewall, or WAF, is a security measure that can help to protect your API from attack. A WAF works by inspecting incoming traffic and blocking requests that appear to be malicious. This can help to prevent attackers from injection SQL code into your API or from launching cross-site scripting attacks.
While a WAF is not a silver bullet, it can be an effective way to add an extra layer of defense. When configuring a WAF, be sure to keep an eye out for false positives. If your WAF is too aggressive, it may block legitimate traffic, causing disruptions for your users.
Monitor your API for suspicious activity.
When it comes to building a secure API, you need to be vigilant about monitoring for suspicious activity. Internal REST APIs in the cloud are especially vulnerable to attack, so it’s important to have a monitoring solution in place that can detect and respond to threats quickly.
There are a few different ways to monitor your API for suspicious activity, but one of the most effective is to use a dedicated API security platform. These platforms provide real-time visibility into all API activity, so you can quickly identify and respond to any potential threats.
In addition, they offer features like rate limiting and fraud detection that can help to further protect your API. By using a dedicated API security platform, you can rest assured that your API is safe from attackers.
Conclusion
All in all, following these best practices for securing your internal REST API will give you peace of mind that your data is safe and sound. And if you’re ever feeling unsure about how to proceed or are struggling with an implementation, our team is always here to help – just reach out!





