We all know that configuration changes in the cloud can sometimes open up unexpected vulnerabilities. And when it comes to the AWS cloud, Amazon Route 53 is a crucial service that requires constant vigilance for any risky changes.
Let’s dive into some tips and best practices to secure your AWS Route 53 and keep your cloud fortress safe from unwanted surprises.
Understanding AWS Route 53
AWS Route 53 is a popular DNS service provided by AWS, handling millions of top-level and sub-domains. While it’s an essential tool for many organizations, it can also be a bit tricky to configure correctly. If not set up properly, it might expose your cloud to potential risks.

Risks and Challenges
Now, you might wonder, what are these risks exactly? Well, it doesn’t always take a massive attack to cause trouble in your cloud.
Even simple configuration changes can unexpectedly increase your attack surface. And while AWS Shield can defend against DDoS attacks, it won’t guard you against risky changes to your Route 53 configuration.
High-level risks include registering new domains, deleting domains, and managing DNS records. To maintain a strong DNS posture, we need to keep a watchful eye on any changes in our Route 53 account.
A Scary Proof-of-Concept
Real-world incidents have shown how important it is to keep track of new domain registrations and deletions. Just imagine someone rerouting your Route 53 domains without your knowledge, resulting in significant losses!
A security researcher demonstrated how scanning for registered domain names for S3 buckets could lead to bucket takeovers. This proof-of-concept revealed the connection between AWS Route 53 DNS records and the rest of your AWS infrastructure.
In one case, a BGP hack rerouted domains for AWS Route 53, resulting in the theft of cryptocurrency worth $150,000. While Amazon Route 53 itself wasn’t compromised, this event highlighted the need to closely track domain creations in Route 53.
Scary stuff, right?
AWS Route 53 Security Best Practices
At the core, knowing your domains in Route 53 is crucial.
Real-time alerts for any domain creations or deletions are essential too. AWS maintains a general best practices page, and you can find more security practices in the CIS Amazon Web Services Three-tier Web Architecture Benchmark from the Center for Internet Security.
| The best practices include for example | Set TTLs appropriately to afford to wait for a change to take effect Ensure Root Domain Alias Record Points to ELB Ensure a DNS alias record for the root domain |
| Risky changes that need to be monitored as a best practice these include | Associate VPC with Hosted Zone Change Resource Record Sets Register Domain |
Monitoring Risky Changes with CloudTrail
AWS provides us with CloudTrail, which acts as an extensive audit log for all actions in your AWS environment. However, CloudTrail alone can’t differentiate between valid changes and those that increase your attack surface. Additionally, it lacks an alerting and reporting mechanism.
Automated Solution
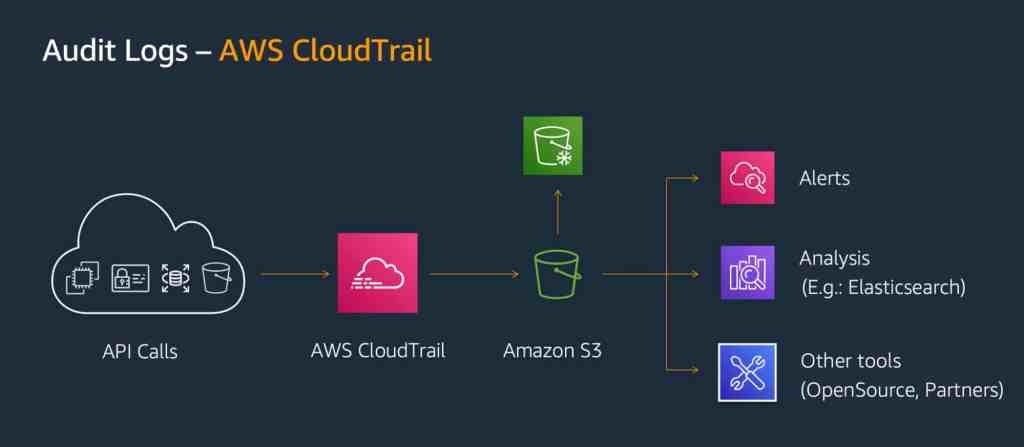
Manually finding risky changes in a vast CloudTrail log is like searching for tiny needles in a massive haystack – not practical or scalable. For effective real-time alerting, reporting, and role-based access control, we need an automated solution that provides a dashboard for visualization and professional features to stay on top of events.
Introducing CD Cloud Logix X CloudTrail:
As much as building custom solutions using native AWS tools sounds enticing, it’s not always the most efficient option. CD Cloud Logix is here to save the day! We offer a complete solution with a team of cloud developers at your disposal, ensuring your AWS Route 53 is secure and your cloud remains a safe haven.
Remember, when it comes to protecting your AWS cloud, a proactive and automated approach with CD Cloud Logix is the way to go. Stay ahead of the game and keep your cloud fortress fortified!





